175 Malicious npm Packages with 26,000 Downloads Used in Credential Phishing Campaign
Summary
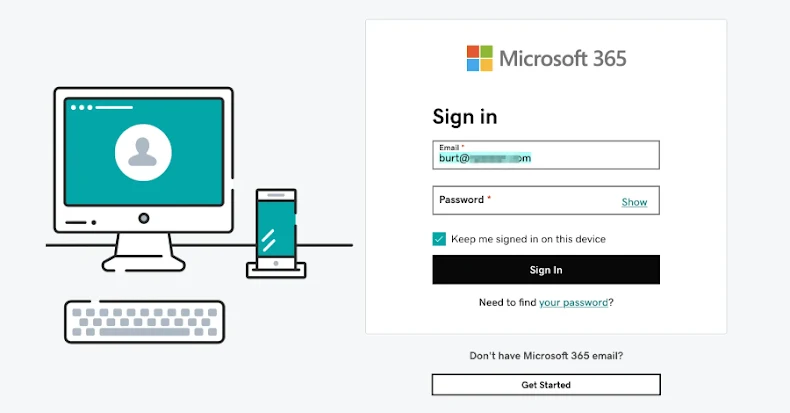
Security researchers (Socket) have uncovered 175 malicious npm packages that together have been downloaded about 26,000 times and are serving as hosting infrastructure for a credential-phishing campaign dubbed “Beamglea.” Rather than containing install-time payloads, these packages host redirect scripts via npm’s public registry and unpkg.com’s CDN to funnel victims to pre-filled Microsoft credential-harvesting pages.
The campaign uses an automated Python tool, “redirect_generator.py,” to publish packages named like “redirect-xxxxxx”, inject a victim’s email and a phishing URL, then create HTML files that reference a CDN-served JavaScript (beamglea.js). When victims open the crafted HTML files, the script redirects them to phishing pages with the email pre-filled via the URL fragment, increasing believability and success rates. Socket found over 630 HTML files in the packages’ outputs and notes the actor published packages across nine accounts to build resilient, zero-cost hosting for the scam.
Key Points
- 175 malicious npm packages observed, collectively ~26,000 downloads.
- Campaign codename: Beamglea — targeted more than 135 organisations in industrial, technology and energy sectors.
- Attackers used an automated “redirect_generator.py” to publish packages named “redirect-xxxxxx” and inject victim-specific data.
- unpkg.com CDN is abused to serve a beamglea.js redirect script that sends victims to Microsoft credential-harvesting pages with emails pre-filled.
- Over 630 crafted HTML files (masquerading as invoices, specs, orders) were found; distribution method likely email with attachments or links.
- Packages do not run malicious code on install — npm/unpkg are abused as free, trusted infrastructure rather than a direct code-execution vector.
Why should I read this?
Short version: this is clever and annoying. Attackers are using the npm registry and trusted CDNs as free hosting to make phishing pages look legit — and they pre-fill your email to trick you faster. If you manage code, email security, or user access, a quick read will save you from being the next target.
Context and Relevance
This incident highlights a growing trend where threat actors weaponise legitimate developer infrastructure and CDNs to host phishing infrastructure at scale. It shifts the problem away from malicious packages executing on install to abused hosting and distribution — making detection harder because the registry itself appears benign.
Defensive takeaways: monitor for suspicious package names (eg. redirect-xxxx), watch for unpkg or CDN references in unexpected HTML/email attachments, enforce strong MFA and phishing-resistant authentication, tighten mail gateway scanning for HTML attachments that load external scripts, and include registry/CDN misuse in threat-hunting playbooks. Organisations should also consider automated scanning of inbound HTML and block known malicious CDN paths where practical.
Source
Source: https://thehackernews.com/2025/10/175-malicious-npm-packages-with-26000.html