Astaroth Banking Trojan Abuses GitHub to Remain Operational After Takedowns
Summary
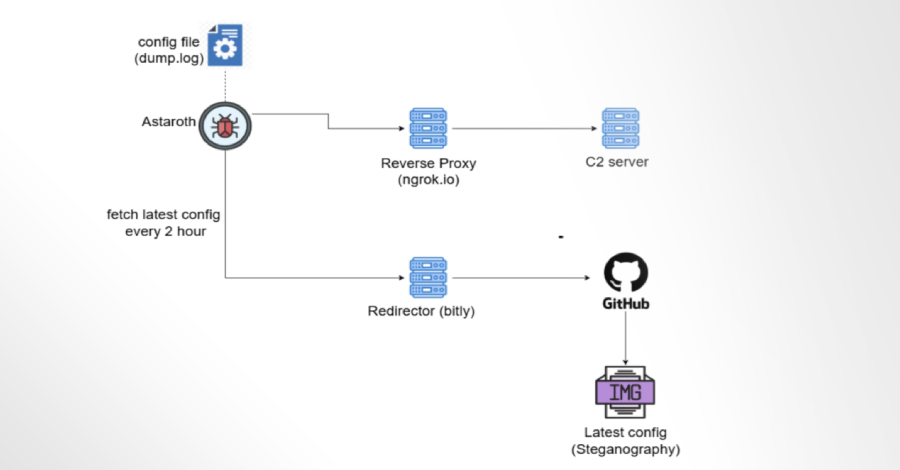
Researchers at McAfee Labs have uncovered a campaign in which the Astaroth banking trojan uses GitHub repositories as a fallback configuration and command channel to stay resilient after takedowns. The threat — focused largely on Brazil but active across Latin America — is distributed via DocuSign-themed phishing messages that deliver a zipped Windows .lnk shortcut containing obfuscated JavaScript. That chain fetches further scripts, runs an AutoIt component, injects a Delphi DLL into a RegSvc.exe process and runs Astaroth, which monitors banking and crypto sites and exfiltrates credentials via an Ngrok reverse proxy.
Key Points
- Astaroth operators host steganographed configuration images on GitHub to replace traditional C2 servers when they are taken down.
- Distribution begins with DocuSign-style phishing that drops a .lnk shortcut containing obfuscated JavaScript and subsequently an AutoIt payload.
- The malware injects a Delphi-based DLL into RegSvc.exe, monitors browser windows for banking/crypto sites and captures credentials (keylogging).
- Exfiltration is handled through Ngrok reverse proxies; targeted sites include major Brazilian banks and crypto services.
- Astaroth includes anti-analysis checks (emulator/debugger detection) and persistence via a Startup LNK that launches on reboot; it geofences and avoids English/US locales.
- McAfee worked with Microsoft/GitHub to remove the repositories, temporarily disrupting the actors’ fallback channel.
Content summary
The article explains the full attack chain: phishing → .lnk with obfuscated JavaScript → download and execution of AutoIt → shellcode execution → Delphi DLL decrypts and injects Astaroth into a process. Astaroth watches for banking/crypto browser windows, hooks keyboard events to log credentials, and sends stolen data back via Ngrok. When primary C2 servers become unreachable, the trojan retrieves updated configuration from images hosted on GitHub (using steganography) so operators can pivot and keep infections alive despite takedowns.
Context and Relevance
Using reputable platforms like GitHub for fallback C2/configuration is an emerging trend that complicates takedowns — hosting appears legitimate, and removal requires platform cooperation. This campaign highlights how commodity malware families continue to evolve their infrastructure resilience and blend multiple technologies (AutoIt, Delphi, Ngrok, steganography) to avoid disruption. Organisations, security teams and incident responders — especially in Latin America — should note the delivery mechanics, persistence strategies and the use of public hosting as a backup control channel.
Why should I read this?
Quick and dirty: if you look after users, bank security or incident response in Brazil/Latin America (or run anti-phishing programmes), this article tells you exactly how Astaroth is getting back online after takedowns — and why a GitHub removal is only a temporary fix. Saves you trawling multiple reports.
Source
Source: https://thehackernews.com/2025/10/astaroth-banking-trojan-abuses-github.html