Researchers Uncover WatchGuard VPN Bug That Could Let Attackers Take Over Devices
Summary
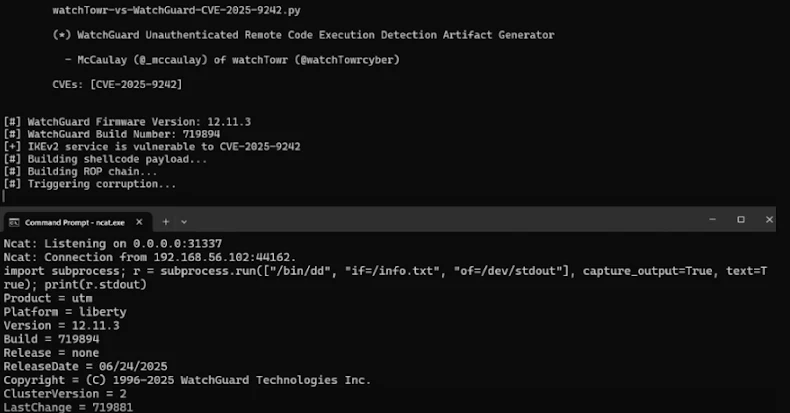
Security researchers have disclosed a critical out-of-bounds write vulnerability in WatchGuard Fireware OS (CVE-2025-9242, CVSS 9.3) that can be triggered during the IKEv2 handshake. The flaw stems from a missing length check in the function that handles client identification in the IKE process, enabling unauthenticated attackers to achieve remote code execution on internet-exposed appliances.
WatchGuard has released fixes across supported branches (2025.1.1, 12.11.4, 12.3.1_Update3, 12.5.13) and noted that 11.x has reached end-of-life. Research by watchTowr Labs demonstrates an exploit chain that can spawn an interactive Python shell via mprotect()-based techniques and then escalate to a full Linux shell by remounting and installing BusyBox — a practical path for adversaries to obtain persistent control of perimeter devices.
Key Points
- CVE-2025-9242 is an out-of-bounds write in WatchGuard Fireware OS affecting several 11.x, 12.x and 2025.1 releases (CVSS: 9.3).
- The bug exists in ike2_ProcessPayload_CERT which copies a client identification into a 520-byte stack buffer without proper length validation.
- It is exploitable pre-authentication during the IKE_SA_AUTH phase of IKEv2, affecting mobile user and branch office VPNs when configured with dynamic gateway peers.
- watchTowr Labs showed a realistic weaponisation path: control of instruction pointer → mprotect() to bypass NX → Python interactive shell over TCP → remount FS, deploy BusyBox → full /bin/sh.
- WatchGuard has issued patches: 2025.1.1, 12.11.4, 12.3.1_Update3, 12.5.13; 11.x is EOL and should be replaced.
- Immediate mitigations: patch urgently, restrict IKEv2 access to trusted networks, apply network segmentation and firewall rules, and monitor for suspicious IKE traffic and indicators of compromise.
Context and Relevance
This vulnerability matters because it targets VPN infrastructure — a high-value, internet-exposed attack surface that adversaries (including ransomware groups) favour. Pre-authenticated remote code execution on perimeter appliances can lead to rapid network compromise and long-lived footholds. The bug follows a pattern of recent high-severity appliance vulnerabilities (Dell UnityVSA, Telerik, etc.), underlining the need for continuous patching and tighter management-plane controls.
Author style
Punchy: this is not optional reading if you manage WatchGuard kit or perimeter VPNs. The write-up summarises the technical root cause and the practical exploit route — if you care about stopping real-world attacks, patch and lock down access now.
Why should I read this?
Short answer: because it’s the kind of bug that lets attackers waltz past your VPN without credentials and live on your perimeter. We’ve done the digging so you don’t have to — know the CVE, the affected versions, the patch that fixes it, and the immediate steps to reduce risk.
Source
Source: https://thehackernews.com/2025/10/researchers-uncover-watchguard-vpn-bug.html