Novel clickjacking attack relies on CSS and SVG
Summary
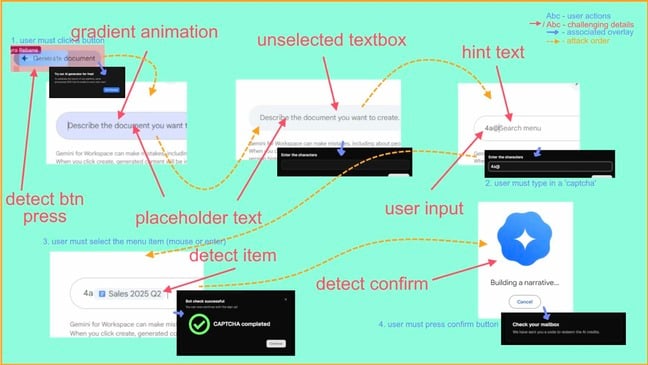
Security researcher Lyra Rebane has devised and demonstrated a new clickjacking technique that uses SVG filters and CSS to read and process pixels across origins, effectively bypassing same-origin protections in some scenarios. Shown at BSides Tallinn and documented in a blog post and PoC, the technique leverages SVG filter primitives (notably feBlend and feComposite) to build logic gates and perform non-JavaScript computation on visual data. That lets an attacker probe framed or injected content and carry out clickjacking or data-exfiltration flows — Rebane demonstrated a PoC that can extract text from a Google Docs session.
The issue is not yet universally fixed and appears to affect multiple browsers (Rebane reports impacts on Chromium and Firefox). Google issued a bug bounty for the report but a related Chromium bug was previously marked “won’t fix,” so remediation is unclear. Defences include traditional framing protections (X-Frame-Options / CSP frame-ancestors), Content Security Policy to block unsafe injection, and using APIs like Intersection Observer v2 to detect when an SVG filter overlays an iframe.
Key Points
- Lyra Rebane demonstrated an SVG/CSS-based clickjacking technique that can access and process pixels from cross-origin content.
- The attack constructs logic gates with SVG filter primitives (feBlend, feComposite) to perform arbitrary, non-timing-based computation on page pixels.
- Proof-of-concept shows exfiltration of Google Docs text via a framed UI flow and a CAPTCHA-style interaction.
- Vulnerability affects framing and can be abused with HTML injection where JavaScript is blocked, making CSS+SVG a powerful non-JS attack vector.
- Not yet universally fixed; Google awarded a bug bounty of $3,133.70 but it remains unclear whether the root cause is a browser bug.
- Mitigations: prevent framing with X-Frame-Options or CSP frame-ancestors, use CSP to limit injection, and detect overlays with Intersection Observer v2.
Why should I read this?
Because it’s a clever way to break things without JavaScript — and that means sites you thought were safe (framed embeds, or pages that block JS) might still leak data. If you build or defend web apps, or run services that get embedded, this is the sort of nifty trick that saves attackers hassle and gives them new options. Read the detail so you know what to patch or guard against.
Source
Source: https://go.theregister.com/feed/www.theregister.com/2025/12/05/css_svg_clickjacking/