Researchers Expose TA585’s MonsterV2 Malware Capabilities and Attack Chain
Summary
Cybersecurity researchers at Proofpoint have detailed activity by a previously undocumented threat actor they call TA585, which has been distributing an off‑the‑shelf malware family named MonsterV2 via targeted phishing and website injection campaigns. TA585 is notable for running its own end‑to‑end infrastructure — from delivery to installation — rather than outsourcing distribution.
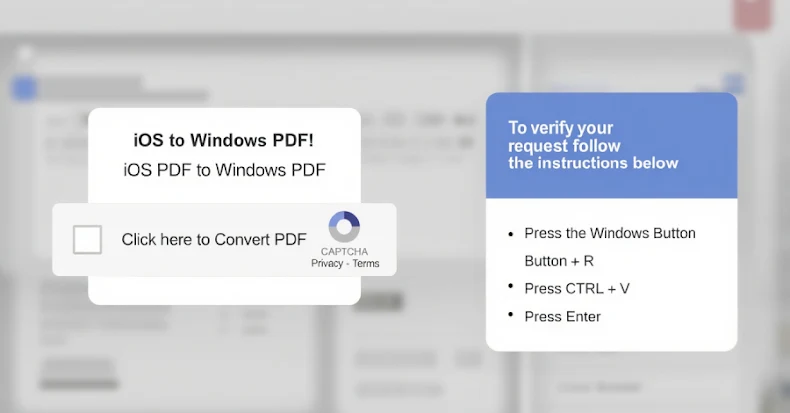
MonsterV2 functions as a RAT, stealer and loader. It is delivered through IRS‑themed phishing lures, ClickFix social engineering overlays injected into legitimate sites, and even fake GitHub security alerts. The malware is commonly packed with the SonicCrypt C++ crypter to evade analysis and supports a wide range of post‑infection capabilities including HVNC, clipboard clippers for crypto theft, keylogging, screenshots, file exfiltration and remote command execution.
Key Points
- TA585 manages its own delivery chain and infrastructure rather than buying access or using third‑party distributors.
- MonsterV2 (aka Aurotun Stealer) is a multifunction malware: stealer, loader and RAT with HVNC and clipper features.
- Primary delivery methods observed: IRS‑themed phishing URLs to PDFs, ClickFix overlays via JavaScript web injects, and fake GitHub tag notifications.
- Earlier waves used Lumma Stealer; TA585 moved to MonsterV2 in early 2025 and reuses some infrastructure linked to Rhadamanthys and CoreSecThree frameworks.
- MonsterV2 is typically packed with SonicCrypt and performs anti‑debug/sandbox checks, privilege escalation attempts and persistence (the “aurotun” option).
- The malware communicates with C2 servers, sends system and geolocation info (via api.ipify[.]org), and supports commands to exfiltrate data, run shells, manage processes, start HVNC, keylog and deploy additional payloads like StealC and Remcos.
- The actor sells MonsterV2 as a service: Standard at $800/month and Enterprise at $2,000/month; notably it avoids infecting CIS countries.
Context and Relevance
This report is important because it shows a modern shift: criminal groups increasingly operate full stacks — build, deliver, and manage malware themselves — lowering their dependency on third parties and making campaigns more resilient. The use of web‑injects and ClickFix overlays means even well‑maintained websites can become infection vectors. The wide feature set of MonsterV2 (HVNC, clipper, loader functionality) makes it a flexible tool for diverse criminal goals from credential theft to remote access and subsequent payload distribution.
For security teams, the case underlines the need for layered defences: robust email filtering and URL detonation, monitoring for unusual PowerShell/cmd execution patterns, protection against browser‑injected overlays, and careful scrutiny of unexpected GitHub notices or tagging behaviour affecting corporate accounts.
Author’s take
Punchy summary: TA585 isn’t a hit‑and‑run gang — it’s running a repeatable, professionalised malware service. Read the details if you want to know how they trick users and what to look for in logs.
Why should I read this
Quick and blunt — this one’s useful if you work in security or manage user‑facing systems. It explains fresh delivery tricks (ClickFix via real site injects and fake GitHub alerts) and the capabilities of a commercially sold RAT/stealer. We’ve saved you the deep dive: read this to update email defences, endpoint rules and web‑monitoring checks now.
Source
Source: https://thehackernews.com/2025/10/researchers-expose-ta585s-monsterv2.html